CryptoLocker. WannaCry. DarkSide. Conti. MedusaLocker. The ransomware threat isn’t going away anytime quickly; the inside track brings consistent reviews of recent waves of this pernicious form of malware washing the world over. It’s standard largely as a result of the rapid monetary payoff for attackers: It really works by means of encrypting the information to your laborious disk, then calls for that you just pay a ransom, continuously in Bitcoin or different cryptocurrency, to decrypt them.
However you needn’t be a sufferer. There’s lots that Home windows 10 and 11 customers can do to offer protection to themselves towards it. On this article, I’ll display you how you can stay your self protected, together with how you can use an anti-ransomware instrument constructed into Home windows.
(Directors, see “What IT must find out about ransomware and Home windows” on the finish of this newsletter.)
This newsletter assumes that you just’re already taking the elemental precautions towards malware generally, together with working anti-malware instrument and not downloading attachments or clicking hyperlinks in e mail from unknown senders and suspicious-looking e mail. Additionally notice that this newsletter has been up to date for the Home windows 10 November 2021 Replace (model 21H2) and the Home windows 11 October 2021 Replace (model 21H2). When you have an previous unlock of Home windows 10, some issues could also be other.
Use managed folder get right of entry to
Microsoft is anxious sufficient about ransomware that it constructed an easy-to-configure anti-ransomware instrument immediately into Home windows 10 and Home windows 11. Known as managed folder get right of entry to, it protects you by means of letting best protected and completely vetted programs get right of entry to your information. Unknown programs or identified malware threats aren’t allowed via.
Via default, the function isn’t grew to become on, so if you wish to offer protection to your self towards ransomware, you’ll have to inform it to get to paintings. And you’ll be able to customise precisely the way it works by means of including new programs to its whitelist of techniques that may get right of entry to information, and including new folders along with those that it protects by means of default.
To change it on, you’ll want to get right of entry to Home windows Safety. There are a number of tactics to get to it in each Home windows 10 and Home windows 11:
- Click on the up arrow at the left aspect of the taskbar, then click on the Home windows Safety icon — a protect.
- Click on Get started > Settings to open the Settings app, then make a selection Replace & Safety > Home windows Safety in Home windows 10 or Privateness & Safety > Home windows Safety in Home windows 11.
- Use Home windows Seek. In Home windows 10, the quest field is within the taskbar subsequent to the Get started button. In Home windows 11, click on the quest icon at the taskbar to open the quest pane. Sort home windows safety into the quest field subsequent and make a selection Home windows Safety from the effects.
In Home windows Safety, make a selection Virus & risk coverage. Scroll all the way down to the “Ransomware coverage” phase and click on Arrange ransomware coverage. From the display that looks, beneath “Managed folder get right of entry to,” toggle the transfer to On. You’ll get a suggested asking if you wish to make the alternate. Click on Sure.
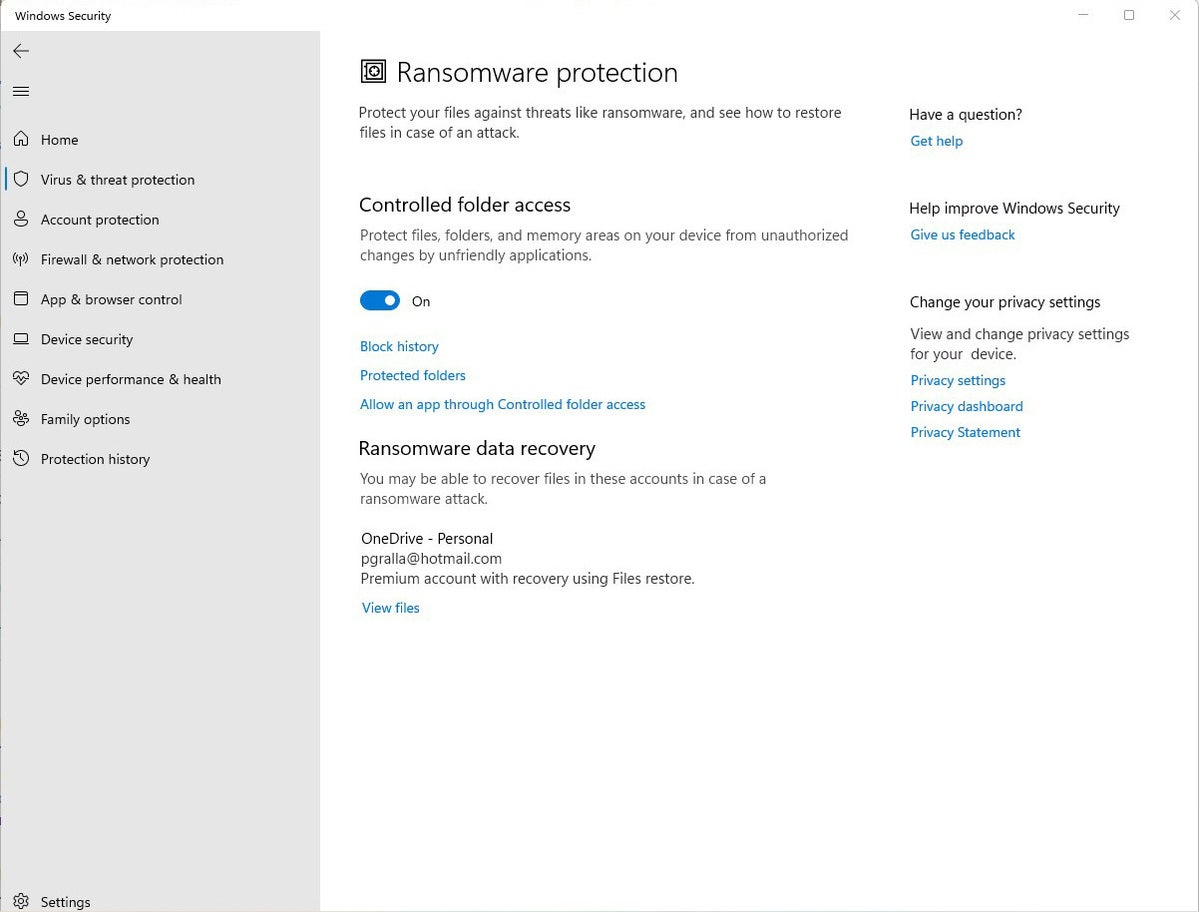 IDG
IDGTransfer the toggle to On to activate managed folder get right of entry to. (Click on symbol to amplify it.)
You shouldn’t depart it at that and really feel protected but, as a result of there’s an opportunity that you’ve folders you’d like to offer protection to that the function ignores. Via default, it protects Home windows machine folders (and folders beneath them) like C:CustomersUserNamePaperwork, the place UserName is your Home windows person identify. Along with Paperwork, Home windows machine folders come with Desktop, Song, Footage, and Movies.
However your entire different folders are honest sport for any ransomware that makes its approach onto your PC. So in the event you use Microsoft’s OneDrive cloud garage, for instance, any OneDrive folders and information to your PC aren’t safe. For the reason that Microsoft is making an attempt to transport everybody it might onto OneDrive, this can be a sudden omission.
So as to add folders you need safe, click on the Secure folders hyperlink that looks after you turn on managed folder get right of entry to. A suggested seems asking if you wish to make the alternate. Click on Sure. Click on the Upload a safe folder button this is on most sensible of the checklist of safe folders that looks, then navigate from the display that looks to the folder you need to offer protection to and click on Make a selection Folder.
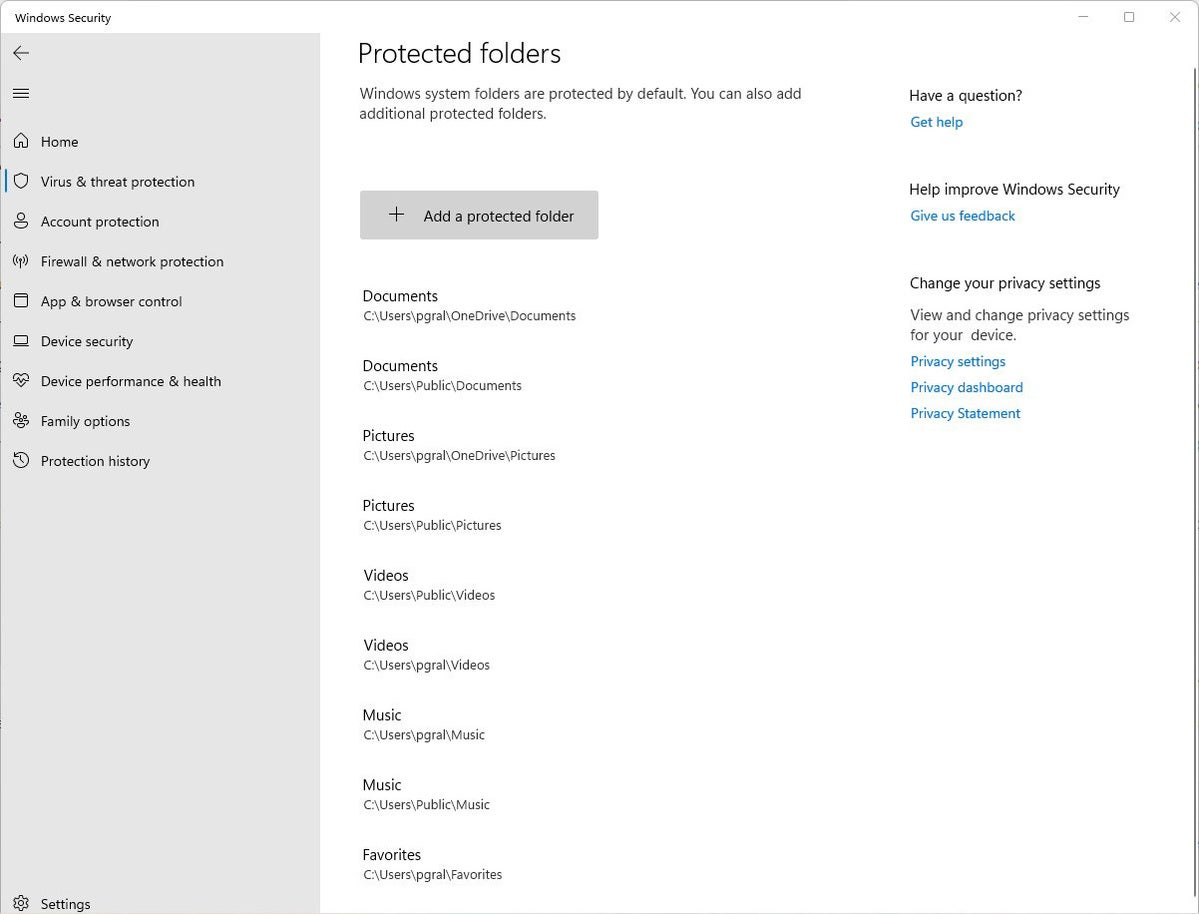 IDG
IDGClick on Upload a safe folder to offer protection to extra of your folders with managed folder get right of entry to. (Click on symbol to amplify it.)
Proceed so as to add folders on this approach. Needless to say whilst you upload a folder, all folders beneath it are safe as smartly. So in the event you upload OneDrive, for instance, there’s no want to upload all the folders beneath it.
(Observe: Relying to your model of OneDrive, you might be able to repair OneDrive information, despite the fact that you don’t keep an eye on them with managed folder get right of entry to. For main points, see the Microsoft documentation “Restore deleted files or folders in OneDrive.”)
If making a decision at any level to take away a folder, get again to the “Secure folders” display, click on the folder you need to take away, after which click on Take away. Observe that you just received’t be capable to take away any of the Home windows machine folders which are safe whilst you flip the function on. You’ll best take away those that you just’ve added.
Microsoft determines which programs will have to be allowed get right of entry to to safe folders, and unsurprisingly, amongst them is Microsoft Administrative center. Microsoft hasn’t printed a listing of which programs are allowed, regardless that, so believe taking motion to let programs you believe get right of entry to your information.
To do it, return to the display the place you grew to become on managed folder get right of entry to and click on Permit an app via Managed folder get right of entry to. A suggested seems asking if you wish to make the alternate. Click on Sure. From the display that looks, click on Upload an allowed app, navigate to the executable document of this system you need so as to add, click on Open, after which verify you need so as to add the document. As with including folders to the checklist of safe folders, you’ll be able to take away the app by means of getting again to this display, clicking the applying you need to take away, then clicking Take away.
Trace: In case you’re now not certain the place executable information are positioned for techniques you need so as to add to the whitelist, search for the folder identify with this system’s identify within the WindowsProgram Recordsdata or WindowsProgram Recordsdata (x86) folders, then search for an executable document in that folder.
Again up… however do it correctly
The entire level of ransomware is to carry your information hostage till you pay to liberate them. So one of the crucial very best protections from ransomware is to again up your information. That approach, there’s no want to pay the ransom, as a result of you’ll be able to simply repair your information from the backup.
However in terms of ransomware, now not all backups are created equivalent. You want to watch out about choosing the proper backup method and repair. It’s a good suggestion to make use of a cloud-based garage and backup carrier somewhat than best backing as much as a force connected on your PC. In case you again as much as a force connected on your PC, when your PC will get inflamed with ransomware, the backup force will probably be encrypted along side another disks within or connected on your PC.
Make certain that your cloud-based garage and backup makes use of versioning — this is, it assists in keeping now not simply the present model of each and every of your information, however earlier ones as smartly. That approach, if essentially the most present model of your information will get inflamed, you’ll be able to repair from earlier variations.
Maximum backup and garage services and products, together with Microsoft OneDrive, Google Pressure, Carbonite, Dropbox and plenty of others, use versioning. It’s a good suggestion to get aware of the versioning function of whichever carrier you utilize now, so you’ll be able to simply repair information in a pinch.
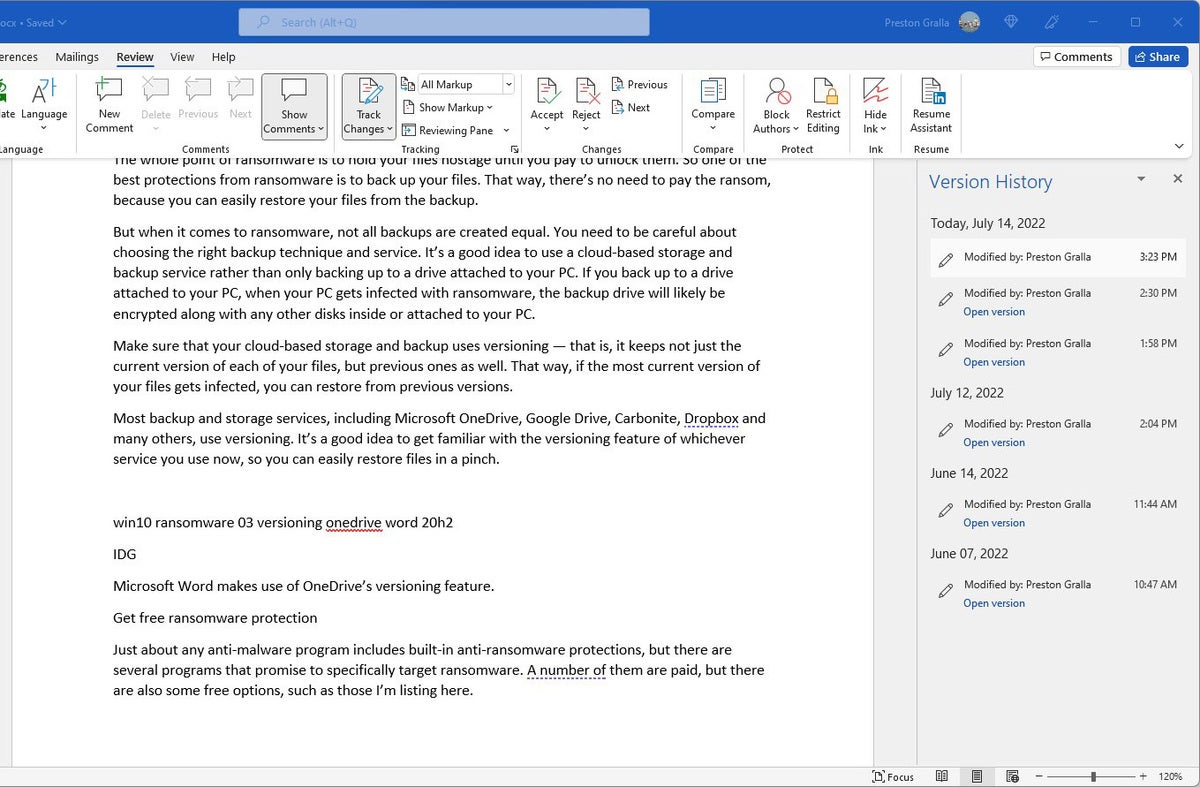 IDG
IDGMicrosoft Phrase uses OneDrive’s versioning features in its Model Historical past function. (Click on symbol to amplify it.)
Get unfastened ransomware coverage
Near to any anti-malware program comprises integrated anti-ransomware protections, however there are a number of techniques that promise to particularly goal ransomware. Various them are paid, however there also are some unfastened choices, corresponding to the ones I’m checklist right here.
Bitdefender offers free decryption tools that can unlock your data in the event you’ve been attacked by means of ransomware and it’s being held ransom. They may be able to best decrypt information that’s been encrypted with sure explicit items or households of ransomware, together with REvil/Sodinokibi, DarkSide, MaMoCrypt, WannaRen and a number of other others. And Kaspersky gives anti-ransomware software for free for each house and industry customers, even if there are barriers at the choice of gadgets you’ll be able to apply it to.
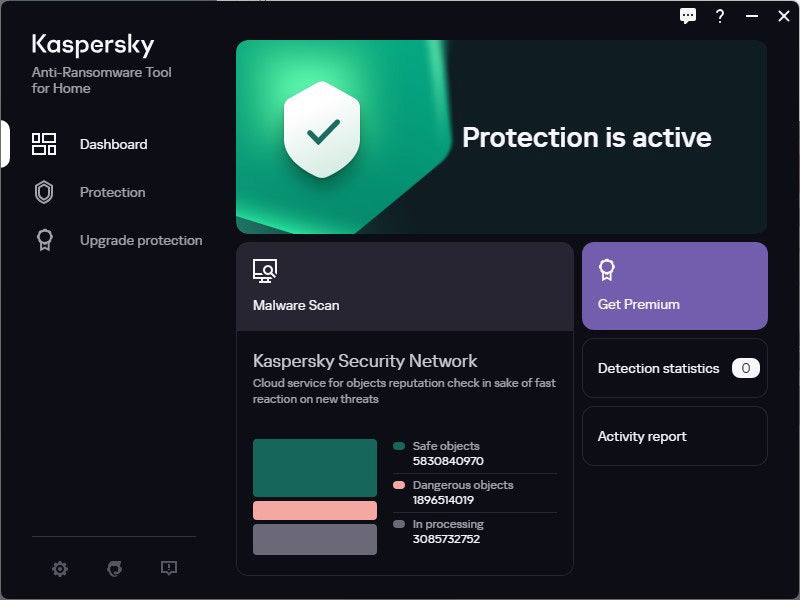 IDG
IDGKapersky’s unfastened anti-ransomware instrument. (Click on symbol to amplify it.)
Keep patched
Microsoft often releases Home windows 10 and Home windows 11 safety patches, they usually’re routinely carried out by way of Home windows Replace. However in the event you listen a couple of ransomware outbreak, you shouldn’t look forward to Home windows Replace to paintings — you will have to in an instant get the replace your self in order that you’re safe once imaginable. And it’s now not simply Home windows updates you need to get. You additionally need to be sure that Home windows Safety, Microsoft’s integrated anti-malware instrument, has the newest anti-malware definitions.
To do each in Home windows 10, move to Settings > Replace & Safety > Home windows Replace and click on the Test for updates button. In Home windows 11, move to Settings > Home windows Replace and click on the Test for updates button. (If updates are already looking forward to you, you’ll see them indexed as a substitute of the Test for updates button.) If Home windows reveals updates, it installs them. If it calls for a reboot, it’s going to let you know.
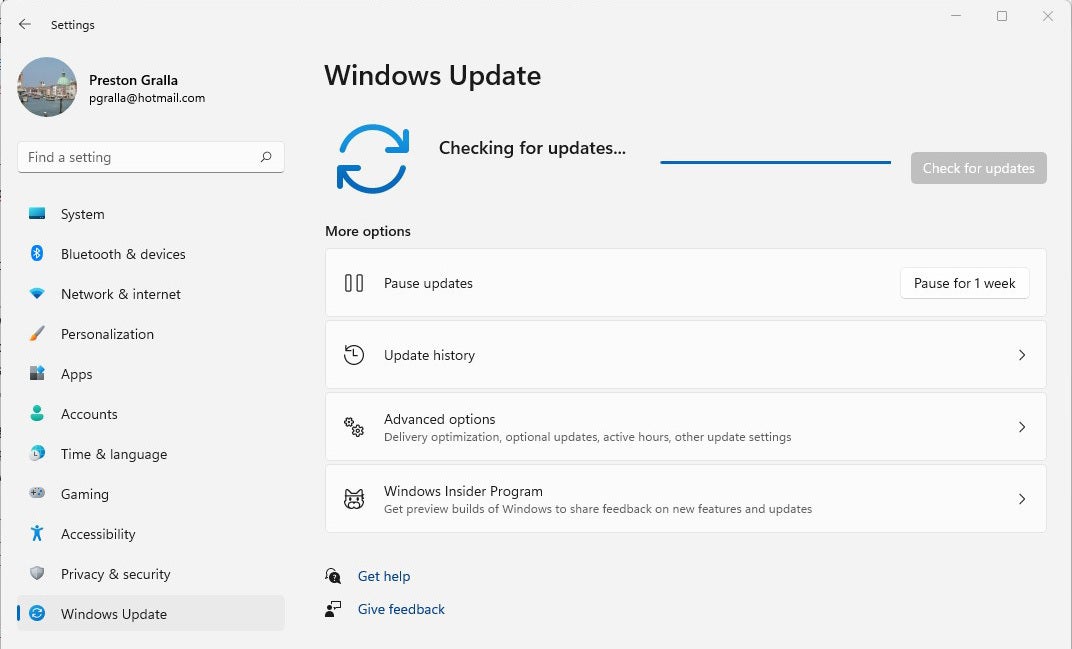 IDG
IDGChecking for Home windows 11 updates. (Click on symbol to amplify it.)
You want to fret now not almost about Home windows staying patched, however different instrument as smartly. In case you use an anti-malware program instead of Home windows Safety, be sure that it and its malware definitions are up-to-the-minute.
And the opposite instrument to your PC will have to be saved up-to-the-minute as smartly. So take a look at how each and every piece of instrument will get up to date and be sure you replace each and every one often.
Disable macros in Microsoft Administrative center
Ransomware may also be unfold via macros in Office files, in an effort to be protected you will have to flip them off. Microsoft now disables them by means of default, however that doesn’t essentially imply that they’re grew to become off on your model of Administrative center, relying on whilst you put in it and whether or not you’ve up to date it. To show them off, whilst you’re in an Administrative center software, make a selection Document > Choices > Believe Middle > Believe Middle Settings and make a selection both Disable all macros with notification or Disable all macros with out notification. In case you disable them with notification, whilst you open the document you’ll get a message caution that the macros have been disabled and letting you flip them on. Most effective flip them on in the event you’re completely certain they’re from a protected, relied on supply.
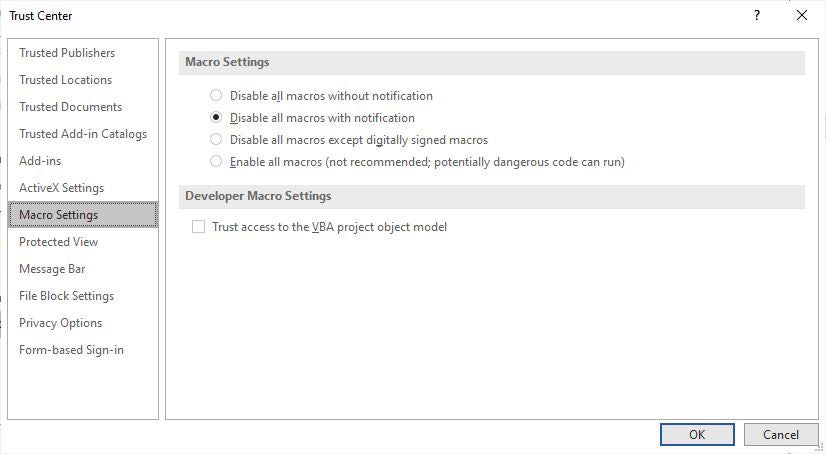 IDG
IDGRight here’s how you can disable macros in Administrative center. (Click on symbol to amplify it.)
What IT must find out about ransomware and Home windows
There’s lots that IT can do to stay firms unfastened from ransomware. The obvious: Practice the newest safety patches not to simply all PCs in a company, however all servers and another enterprise-level {hardware}.
That’s only a get started, regardless that. IT must disable the notoriously insecure SMB1 Home windows networking protocol. A couple of ransomware assaults have unfold during the 30-year-old protocol; even Microsoft says it will have to be utilized by no person, ever.
The excellent news is that Home windows 10 model 1709, launched in October 2017, in the end did away with SMB1. (It’s now not in Home windows 11, both.) However that’s just for PCs with blank installs of model 1709 or later, together with new PCs that experience pop out since then. Older PCs that have been up to date from previous variations of Home windows nonetheless have the protocol inbuilt.
There are a couple of puts IT can move to get lend a hand to show it off. A excellent position to begin is the SMB Security Best Practices document from US-CERT, run by means of the U.S. Division of Native land Safety. It recommends disabling SMB1, after which “blocking off all variations of SMB on the community boundary by means of blocking off TCP port 445 with comparable protocols on UDP ports 137-138 and TCP port 139, for all boundary gadgets.”
The Microsoft give a boost to article “How to detect, enable and disable SMBv1, SMBv2, and SMBv3 in Windows” gives information about how you can flip off the protocol. It recommends killing SMB1 however protecting SMB2 and SMB3 lively, and best deactivating them for brief troubleshooting. For essentially the most up-to-date and detailed details about turning off SMB1, move to the Microsoft TechNet article “Disable SMB v1 in Managed Environments with Group Policy.”
Directors can use the Managed Folder Get entry to function (coated previous on this article) to prevent ransomware from encrypting information and folders of PCs working Home windows 11 or Home windows 10 model 1709 or later. They may be able to use the Crew Coverage Control Console, the Home windows Safety Middle, or PowerShell to activate Managed Folder Get entry to for customers on a community, customise which folders will have to be safe, and let further programs get right of entry to the folders past the Microsoft defaults. For directions, move to the Microsoft article “Enable controlled folder access” to show it on, and to “Customize controlled folder access” to customise which folders will have to be safe and which programs will have to be allowed via.
One possible factor with Managed Folder Get entry to is that it would block apps that customers normally use from getting access to folders. So Microsoft recommends the usage of audit mode first, to look what is going to occur when Managed Folder Get entry to is grew to become on. For details about how you can do it, move to Microsoft’s “Evaluate exploit protection” documentation.
As famous above, Administrative center macros can unfold ransomware. Microsoft is now blocking off macros downloaded from the web by means of default, however to be protected, IT will have to use Crew Coverage to dam them. For recommendation on how you can do it, move to the “Block macros from running in Office files from the Internet” phase on Microsoft’s “Macros from the internet will be blocked by default in Office” documentation and to its “Helping users stay safe: Blocking internet macros by default in Office” weblog put up.
Base line
The excellent news in all this: Home windows 10 and Home windows 11 have explicit anti-ransomware options constructed proper in. Practice the recommendation we’ve defined right here to stay the ransomware risk at bay.
This newsletter was once in the beginning printed in January 2018 and maximum not too long ago up to date in August 2022.
Copyright © 2022 IDG Communications, Inc.


